 Front page > Technology peripherals > Hackers recover $3 million in bitcoin from software wallet locked for over a decade
Front page > Technology peripherals > Hackers recover $3 million in bitcoin from software wallet locked for over a decade
Hackers recover $3 million in bitcoin from software wallet locked for over a decade
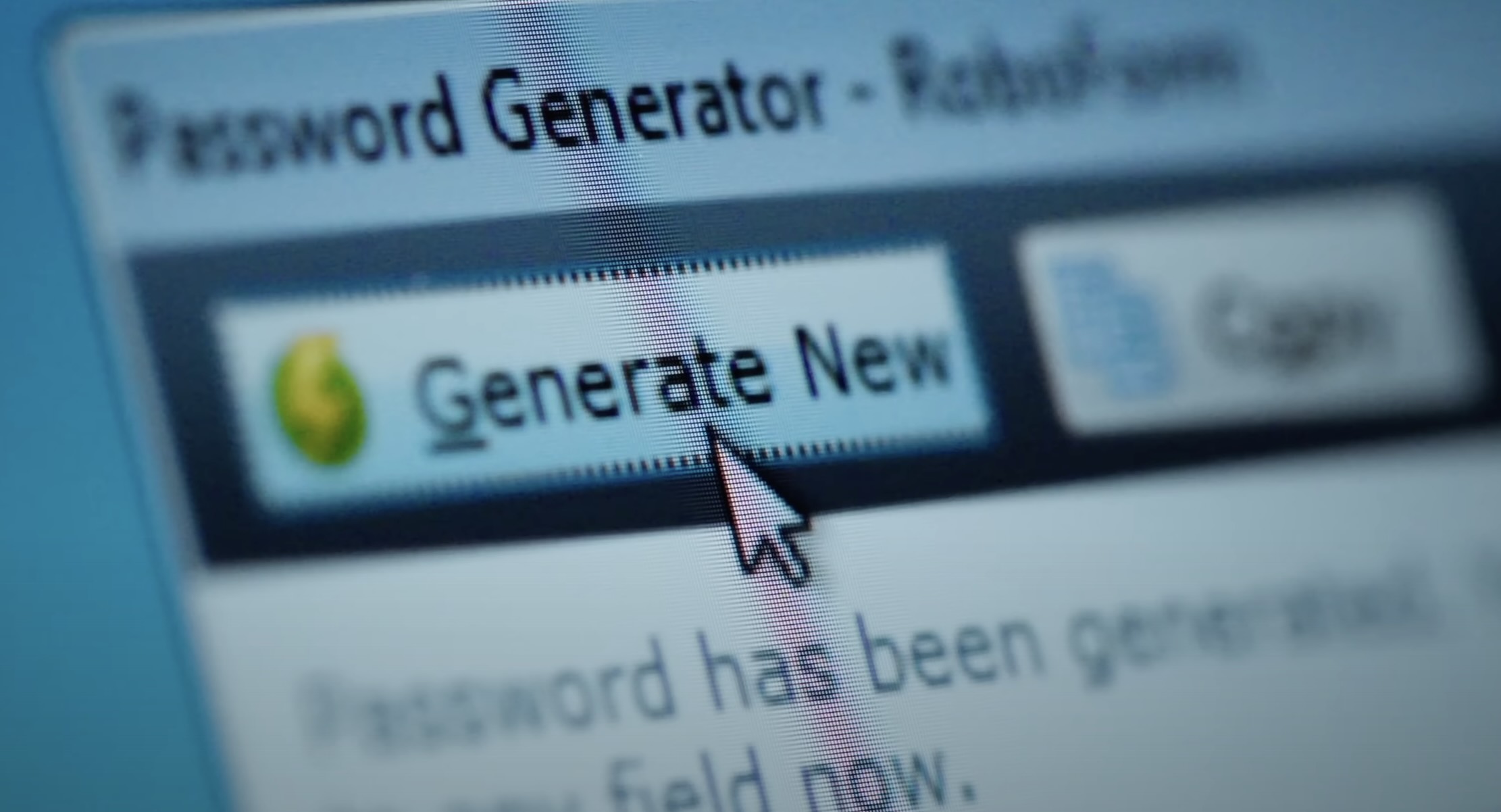
Joe Grand - an ethical hacker and YouTuber who is widely known for his projects involving crypto wallets, has successfully recovered a life-changing amount of bitcoin, presently valued north of $3 million from a software wallet that has been locked for more than a decade. This splendid technical feat was the result of some serious reverse engineering and bug-hunting conducted by Joe and his friend Bruno, who also happens to be a hacking heavyweight.
The premise
The titular Bitcoin wallet was secured using a complex, 20-character password generated by the famous password generation software called RoboForm. Its owner, Michael, had used the software to generate a secure password, which was then stored in a TrueCrypt container. As luck would have it, the encrypted partition became corrupted, abandoning Michael without any recourse, and rendering his funds inaccessible.
Given the massively complex and lengthy nature of the password, traditional brute-forcing attacks were completely unrealistic. Put into perspective by Joe, the probability of being able to correctly 'guess' the password would be as troublesome as finding a specific drop of water in all of Earth's oceans - a task that a mere mortal could never hope to achieve. However, they say where there is desire, there will always be means, and Joe would soon achieve a major step forward
The first breakthrough
Enter Bruno - a fellow ethical hacker, and Joe Grand's frequent collaborator. Bruno's extensive experience in reverse-engineering software would soon prove to be a boon leading to the project's success. Considering the insurmountable nature of a brute-force attack, the duo turned to hunting for vulnerabilities within RoboForm's password generation function. Upon perusing RoboForm's change log (which records changes and bug fixes to the software), they discovered older versions of RoboForm had a critical flaw - the 'random' generation of the password was not random at all. So in essence, by recreating the situational variables that the software used to generate passwords, it would, theoretically, be possible to recreate exact passwords.
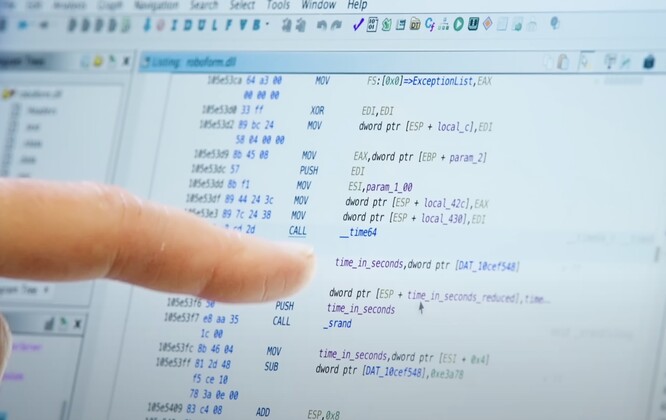
Ghidra to the rescue
For this next part, it is important for us to know whatGhidraandCheat Enginereally do. Both of them, are powerful tools widely used to analyze and reverse engineer or 'decompile' software. Developed by theNSA, Ghidra allows for software decompilation, thus enabling engineers to probe the underlying code of a certain program, helping in finding vulnerabilities and flaws that can then be used to create exploits. Cheat Engine, on the other hand, is a memory scanning tool that lets the user scan and modifies the program's memory while it is in execution, allowing for behavior modification in real-time.
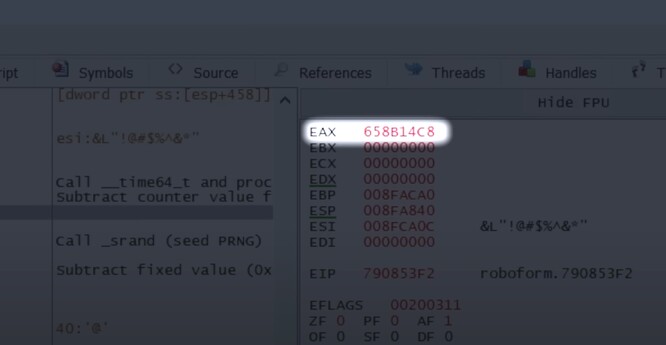
Using the aforementioned tools, the team was able to do the impossible. They dove into RoboForm's inner workings, locating the very specific segment of code responsible for the actual password generation. Upon further inspection, they discovered that the function actually used the system time as a seed value of sorts to generate a password. This is the exact opposite of what you'd expect from password-generation software, because the resulting password could then easily be recreated simply by changing the system time. However for Michael, what was essentially a flaw, would soon turn out to be his safety net.
Hacking 'time'
Utilizing their newfound discovery, the team consisting of Joe & Bruno developed a method to roll back the system time to when Michael claimed he created the password - a 50-day period. They recreated all the potential passwords in the date range by adjusting the time seed value, hoping to find the password generated at that exact past moment. By doing so, the list of potentially correct passwords was reduced exponentially, making a brute-force attack far more effective than before.
But the grind didn't end there. The team encountered several more hurdles involving software crashes and exhausting debugging sessions, but their persistence finally paid off. Upon slightly modifying Michael's initially provided parameters, which now excluded special characters, the team ultimately stumbled upon an exact match. Having struck gold, Bruno announced his victory to Joe through a single text message - 'Success'.
The successful recovery of the 43 BTC - worth over $3 million now, is not only a significant financial relief for the owner but also highlights the undeniable expertise and perseverance of the hacker duo. But it goes without saying, that RoboForm has since addressed the vulnerability, which will make any more recent passwords significantly more tedious to crack, perhaps even impossible. Thus, it is not only necessary to create strong passwords, but also to keep them securely managed.
Disclaimer: The information reported here should not be used as a basis for any personal investment decision. Notebookcheck does not offer cryptocurrency, NFT, or other trading, investment, or financial advice.
-
 INZONE M9 II: Sony launches new \'perfect for PS5\' gaming monitor with 4K resolution and 750 nits peak brightnessThe INZONE M9 II arrives as a direct successor to the INZONE M9, which is now a little over two years old. Incidentally, Sony has also presented the I...Technology peripherals Published on 2024-12-21
INZONE M9 II: Sony launches new \'perfect for PS5\' gaming monitor with 4K resolution and 750 nits peak brightnessThe INZONE M9 II arrives as a direct successor to the INZONE M9, which is now a little over two years old. Incidentally, Sony has also presented the I...Technology peripherals Published on 2024-12-21 -
 Acer confirms the announcement date for its Intel Lunar Lake laptopsLast month, Intel confirmed that it will launch the new Core Ultra 200 series chips on September 3rd. Acer has now announced that it will hold its Nex...Technology peripherals Published on 2024-12-21
Acer confirms the announcement date for its Intel Lunar Lake laptopsLast month, Intel confirmed that it will launch the new Core Ultra 200 series chips on September 3rd. Acer has now announced that it will hold its Nex...Technology peripherals Published on 2024-12-21 -
 AMD Ryzen 7 9800X3D tipped for an October launch; Ryzen 9 9950X3D and Ryzen 9 9900X3D to debut next yearLast year, AMD launched the Ryzen 9 7950X3D and Ryzen 9 7900X3D before the Ryzen 7 7800X3D, which dropped a couple of weeks later. Since then, we'...Technology peripherals Published on 2024-12-10
AMD Ryzen 7 9800X3D tipped for an October launch; Ryzen 9 9950X3D and Ryzen 9 9900X3D to debut next yearLast year, AMD launched the Ryzen 9 7950X3D and Ryzen 9 7900X3D before the Ryzen 7 7800X3D, which dropped a couple of weeks later. Since then, we'...Technology peripherals Published on 2024-12-10 -
 Steam is giving away a very popular indie game, but only todayPress Any Button is an indie arcade game developed by solo developer Eugene Zubko and released in 2021. The story revolves around A-Eye - an artificia...Technology peripherals Published on 2024-11-26
Steam is giving away a very popular indie game, but only todayPress Any Button is an indie arcade game developed by solo developer Eugene Zubko and released in 2021. The story revolves around A-Eye - an artificia...Technology peripherals Published on 2024-11-26 -
 Assassin’s Creed Shadows previews reportedly canceled as Ubisoft backs out of Tokyo Game Show 2024Earlier today, Ubisoft canceled its online appearance at the Tokyo Game Show due to “various circumstances.”This announcement was confirmed via an off...Technology peripherals Published on 2024-11-25
Assassin’s Creed Shadows previews reportedly canceled as Ubisoft backs out of Tokyo Game Show 2024Earlier today, Ubisoft canceled its online appearance at the Tokyo Game Show due to “various circumstances.”This announcement was confirmed via an off...Technology peripherals Published on 2024-11-25 -
 Price of 7-year-old Sony game suddenly doublesThe PlayStation 5 Pro launches at a base price of $700, with the full package, including the drive and stand, reaching up to $850. While Sony argues t...Technology peripherals Published on 2024-11-22
Price of 7-year-old Sony game suddenly doublesThe PlayStation 5 Pro launches at a base price of $700, with the full package, including the drive and stand, reaching up to $850. While Sony argues t...Technology peripherals Published on 2024-11-22 -
 Deal | Beastly MSI Raider GE78 HX gaming laptop with RTX 4080, Core i9 and 32GB DDR5 goes on saleFor gamers who are primarily using their gaming laptop as a desktop replacement, a large notebook like the MSI Raider GE78 HX might be the best choice...Technology peripherals Published on 2024-11-20
Deal | Beastly MSI Raider GE78 HX gaming laptop with RTX 4080, Core i9 and 32GB DDR5 goes on saleFor gamers who are primarily using their gaming laptop as a desktop replacement, a large notebook like the MSI Raider GE78 HX might be the best choice...Technology peripherals Published on 2024-11-20 -
 Teenage Engineering unveils quirky EP-1320 Medieval as world’s first medieval ‘instrumentalis electronicum’That Teenage Engineering is a company that marches to the beat of a very different drummer is no secret – it is in fact what appeals to its many fans....Technology peripherals Published on 2024-11-19
Teenage Engineering unveils quirky EP-1320 Medieval as world’s first medieval ‘instrumentalis electronicum’That Teenage Engineering is a company that marches to the beat of a very different drummer is no secret – it is in fact what appeals to its many fans....Technology peripherals Published on 2024-11-19 -
 Google Photos gets AI-powered presets and new editing toolsThe video editing features present in Google Photos have just received an infusion of AI-backed features, and these changes will improve the user expe...Technology peripherals Published on 2024-11-19
Google Photos gets AI-powered presets and new editing toolsThe video editing features present in Google Photos have just received an infusion of AI-backed features, and these changes will improve the user expe...Technology peripherals Published on 2024-11-19 -
 Tecno Pop 9 5G eyeballs launch with iPhone 16-esque looks and budget specsTecnohas confirmed that it will ditch thegeometriclook of thePop 8for a raised camera hump ostensibly inspired by the newPhone16 and 16 Plusin its suc...Technology peripherals Published on 2024-11-19
Tecno Pop 9 5G eyeballs launch with iPhone 16-esque looks and budget specsTecnohas confirmed that it will ditch thegeometriclook of thePop 8for a raised camera hump ostensibly inspired by the newPhone16 and 16 Plusin its suc...Technology peripherals Published on 2024-11-19 -
 Anker launches new Flow soft touch cable for Apple productsThe Anker Flow USB-A to Lightning Cable (3 ft, Silicone) has arrived at Amazon in the US. The accessory was rumored earlier this year and launched sho...Technology peripherals Published on 2024-11-19
Anker launches new Flow soft touch cable for Apple productsThe Anker Flow USB-A to Lightning Cable (3 ft, Silicone) has arrived at Amazon in the US. The accessory was rumored earlier this year and launched sho...Technology peripherals Published on 2024-11-19 -
 Xiaomi Redmi A27U monitor refreshed with 4K panel and 90W USB C portXiaomi has released various monitors recently, some of which it has offered globally. For reference, the company brought its Mini LED gaming monitor (...Technology peripherals Published on 2024-11-19
Xiaomi Redmi A27U monitor refreshed with 4K panel and 90W USB C portXiaomi has released various monitors recently, some of which it has offered globally. For reference, the company brought its Mini LED gaming monitor (...Technology peripherals Published on 2024-11-19 -
 Tesla Model Y Juniper rival by Huawei will be sold at a lossAs the Model Y Juniper refresh release nears, electric car makers are in a race to launch their own direct competitors to the facelift of Tesla's ...Technology peripherals Published on 2024-11-18
Tesla Model Y Juniper rival by Huawei will be sold at a lossAs the Model Y Juniper refresh release nears, electric car makers are in a race to launch their own direct competitors to the facelift of Tesla's ...Technology peripherals Published on 2024-11-18 -
 Tesla Model Y, Model 3 battery pack loophole keeps US prices low by skirting IRA tax incentive rulesNews recently broke that the Tesla Model 3 LR AWD had regained the full $7,500 US tax incentive thanks to what appeared to be a battery supply switch,...Technology peripherals Published on 2024-11-16
Tesla Model Y, Model 3 battery pack loophole keeps US prices low by skirting IRA tax incentive rulesNews recently broke that the Tesla Model 3 LR AWD had regained the full $7,500 US tax incentive thanks to what appeared to be a battery supply switch,...Technology peripherals Published on 2024-11-16 -
 Find WhatsApp Conversations Faster With New Custom Chat ListsWhatsApp has made it easier to organize your conversations with the global rollout of custom chat lists. This new feature expands on the chat filters ...Technology peripherals Published on 2024-11-16
Find WhatsApp Conversations Faster With New Custom Chat ListsWhatsApp has made it easier to organize your conversations with the global rollout of custom chat lists. This new feature expands on the chat filters ...Technology peripherals Published on 2024-11-16
Study Chinese
- 1 How do you say "walk" in Chinese? 走路 Chinese pronunciation, 走路 Chinese learning
- 2 How do you say "take a plane" in Chinese? 坐飞机 Chinese pronunciation, 坐飞机 Chinese learning
- 3 How do you say "take a train" in Chinese? 坐火车 Chinese pronunciation, 坐火车 Chinese learning
- 4 How do you say "take a bus" in Chinese? 坐车 Chinese pronunciation, 坐车 Chinese learning
- 5 How to say drive in Chinese? 开车 Chinese pronunciation, 开车 Chinese learning
- 6 How do you say swimming in Chinese? 游泳 Chinese pronunciation, 游泳 Chinese learning
- 7 How do you say ride a bicycle in Chinese? 骑自行车 Chinese pronunciation, 骑自行车 Chinese learning
- 8 How do you say hello in Chinese? 你好Chinese pronunciation, 你好Chinese learning
- 9 How do you say thank you in Chinese? 谢谢Chinese pronunciation, 谢谢Chinese learning
- 10 How to say goodbye in Chinese? 再见Chinese pronunciation, 再见Chinese learning
























