Using JavaScript for Secure Encryption in Web Tools
This is a method developers use to help protect sensitive information in a program from potential attackers. The encryption changes the readable data into a coded format that can only be decoded using the correct key; therefore, it is very paramount in securing information such as passwords, financial details, and personal data.
This becomes very critical in times when data breaches and cyberattacks are very rampant. By encrypting the data, a developer will ensure that no unauthorized party intercepts and reads sensitive information during transmission over networks or while it's stored.
Moreover, encryption protects data integrity since it ensures that the data has not been tampered with or changed, and hence users get to their information with an assurance of accuracy and safety. Apart from protecting data, encryption plays a very important role in regulatory compliance. The vast majority of industries are subject to strict laws about data protection, such as Europe's General Data Protection Regulation or the Health Insurance Portability and Accountability Act in the United States.
These laws and regulations often require sensitive data to be encrypted in order to protect a person's private information from unauthorized access. If this is not implemented, the legal penalties are huge, besides damage to the reputation of an organization.
The general case for this is that encryption forms one of the fundamental tools used in protecting data, retaining users' trust, and satisfying legal requirements—the foundation of modern software development, ensuring information remains secure and private in a world of increasing connectivity.
How I Make a Basic Encryption Tool By JavaScript ?
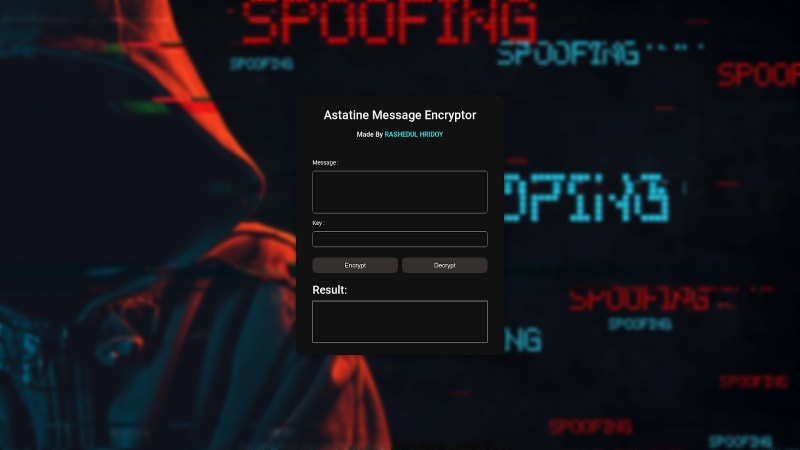
Check: Click Here
Choose an Encryption Algorithm
Any trivial encryption algorithm will do, for instance, a very basic substitution cipher known as the Caesar Cipher which displaces every letter in the text by a specified number of positions down the alphabet.
Define a Function that Encrypts
This function should have as input the text to be encrypted and the value of the shift, that is, by how many places each letter is to be shifted.
Within the function, change each letter in the text into its corresponding value expressed in ASCII. Add the shift to these ASCII values to get the encrypted characters.
Convert the shifted ASCII values back to form the encrypted text.
Implementing Decryption
Now, create a function that decrypts by doing the exact reverse of what you did for encryption.
Take away the value of the shift from the encrypted characters to get the original text.
Testing the Functions
Try out your 'encrypt' and 'decrypt' functions with many different inputs.
This approach will teach you how to encrypt and decrypt in JavaScript. Even though this is a very simple method, it lays a good foundation to understand more complex techniques in encryption like AES (Advanced Encryption Standard) later.
Here is The Source Code Only JavaScript
// Caesar Cipher Encryption Function
function encryptCaesarCipher(text, shift) {
const alphabet = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ';
let encryptedText = '';
// Iterate through each character in the text
for (let i = 0; i
-
 Is the Universal Selector Still a Performance Killer in Modern Browsers?Impact of the Universal Selector on PerformanceThe universal selector (*) applies CSS styles to all elements in a document. While it was once consider...Programming Published on 2024-11-07
Is the Universal Selector Still a Performance Killer in Modern Browsers?Impact of the Universal Selector on PerformanceThe universal selector (*) applies CSS styles to all elements in a document. While it was once consider...Programming Published on 2024-11-07 -
 Is C++11\'s `string::c_str()` Still Null-Terminated?Does C 11's string::c_str() Eliminate Null Termination?In C 11, string::c_str is no longer guaranteed to produce a null-terminated string.Reason...Programming Published on 2024-11-07
Is C++11\'s `string::c_str()` Still Null-Terminated?Does C 11's string::c_str() Eliminate Null Termination?In C 11, string::c_str is no longer guaranteed to produce a null-terminated string.Reason...Programming Published on 2024-11-07 -
 Zipping Options in Effect-TS: A Practical GuideZipping Options in Effect-TS: A Practical Guide In functional programming, combining multiple optional values (represented as Options) in a s...Programming Published on 2024-11-07
Zipping Options in Effect-TS: A Practical GuideZipping Options in Effect-TS: A Practical Guide In functional programming, combining multiple optional values (represented as Options) in a s...Programming Published on 2024-11-07 -
 Elevate Your JavaScript: A Deep Dive into Object-Oriented Programming✨Object-Oriented Programming (OOP) is a powerful paradigm that has revolutionized the way we structure and organize code. While JavaScript began as a ...Programming Published on 2024-11-07
Elevate Your JavaScript: A Deep Dive into Object-Oriented Programming✨Object-Oriented Programming (OOP) is a powerful paradigm that has revolutionized the way we structure and organize code. While JavaScript began as a ...Programming Published on 2024-11-07 -
 How to Capture Multiple Quoted Groups in Go: A Regex SolutionCapturing Multiple Quoted Groups in GoThis article addresses the challenge of parsing strings that follow a specific format: an uppercase command foll...Programming Published on 2024-11-07
How to Capture Multiple Quoted Groups in Go: A Regex SolutionCapturing Multiple Quoted Groups in GoThis article addresses the challenge of parsing strings that follow a specific format: an uppercase command foll...Programming Published on 2024-11-07 -
 From Beginner to Builder: Mastering the Art of PHP ProgrammingWant to learn PHP programming? Step-by-step guide to help you get started! First, install PHP ([Official website](https://www.php.net/)). Master basic...Programming Published on 2024-11-07
From Beginner to Builder: Mastering the Art of PHP ProgrammingWant to learn PHP programming? Step-by-step guide to help you get started! First, install PHP ([Official website](https://www.php.net/)). Master basic...Programming Published on 2024-11-07 -
 Create a Simple Password Manager with HTML, CSS, and JavaScriptAre you tired of using weak passwords or forgetting your login credentials? In this tutorial, we'll create a simple password manager using HTML, C...Programming Published on 2024-11-07
Create a Simple Password Manager with HTML, CSS, and JavaScriptAre you tired of using weak passwords or forgetting your login credentials? In this tutorial, we'll create a simple password manager using HTML, C...Programming Published on 2024-11-07 -
 Why am I getting a 406 (Not Acceptable) Error When Sending a JSON Request to My Spring MVC Controller?Spring JSON Request Returning 406 (Not Acceptable)When attempting to send a JSON request to a Spring MVC controller, some users encounter a "406 ...Programming Published on 2024-11-07
Why am I getting a 406 (Not Acceptable) Error When Sending a JSON Request to My Spring MVC Controller?Spring JSON Request Returning 406 (Not Acceptable)When attempting to send a JSON request to a Spring MVC controller, some users encounter a "406 ...Programming Published on 2024-11-07 -
 How to Easily Identify and Monitor Form Element Events in Chrome DevTools?Understanding Events Triggered by Element InteractionsTo identify and handle events appropriately on a customizable form element, it's essential t...Programming Published on 2024-11-07
How to Easily Identify and Monitor Form Element Events in Chrome DevTools?Understanding Events Triggered by Element InteractionsTo identify and handle events appropriately on a customizable form element, it's essential t...Programming Published on 2024-11-07 -
 Laravel + React project with Authentication & User Panel in less than a minuteI recently posted a video on X where I set up a Laravel React project with authentication and a user profile page in less than a minute! I thought i...Programming Published on 2024-11-07
Laravel + React project with Authentication & User Panel in less than a minuteI recently posted a video on X where I set up a Laravel React project with authentication and a user profile page in less than a minute! I thought i...Programming Published on 2024-11-07 -
 Django Request Life Cycle ExplainedIn the world of web development, understanding the request life cycle is crucial for optimizing performance, debugging issues, and building robust app...Programming Published on 2024-11-07
Django Request Life Cycle ExplainedIn the world of web development, understanding the request life cycle is crucial for optimizing performance, debugging issues, and building robust app...Programming Published on 2024-11-07 -
 Building a Fast and Efficient Semantic Search System Using OpenVINO and PostgresPhoto by real-napster on Pixabay In one of my recent projects, I had to build a semantic search system that could scale with high performance and del...Programming Published on 2024-11-07
Building a Fast and Efficient Semantic Search System Using OpenVINO and PostgresPhoto by real-napster on Pixabay In one of my recent projects, I had to build a semantic search system that could scale with high performance and del...Programming Published on 2024-11-07 -
 How to Eliminate Relative Shift in Matplotlib\'s Tick Labels for Large Numbers?Removing Relative Shift in Matplotlib AxisPlotting against large numbers in Matplotlib can result in an axis with a relative shift for the tick labels...Programming Published on 2024-11-07
How to Eliminate Relative Shift in Matplotlib\'s Tick Labels for Large Numbers?Removing Relative Shift in Matplotlib AxisPlotting against large numbers in Matplotlib can result in an axis with a relative shift for the tick labels...Programming Published on 2024-11-07 -
 Why is the \'r\' Prefix Sometimes Missing in Python Regex?Python Regex: The Enigma of the 'r' PrefixIn the realm of regular expressions in Python, the enigmatic 'r' prefix often sparks questio...Programming Published on 2024-11-07
Why is the \'r\' Prefix Sometimes Missing in Python Regex?Python Regex: The Enigma of the 'r' PrefixIn the realm of regular expressions in Python, the enigmatic 'r' prefix often sparks questio...Programming Published on 2024-11-07 -
 How to Update Dropdown Options Automatically Based on First Dropdown Selection Without a Database?How to Automatically Update Options in a Second Dropdown Based on the Selection in a First Dropdown Without Using a DatabaseYou have two dropdowns whe...Programming Published on 2024-11-07
How to Update Dropdown Options Automatically Based on First Dropdown Selection Without a Database?How to Automatically Update Options in a Second Dropdown Based on the Selection in a First Dropdown Without Using a DatabaseYou have two dropdowns whe...Programming Published on 2024-11-07
Study Chinese
- 1 How do you say "walk" in Chinese? 走路 Chinese pronunciation, 走路 Chinese learning
- 2 How do you say "take a plane" in Chinese? 坐飞机 Chinese pronunciation, 坐飞机 Chinese learning
- 3 How do you say "take a train" in Chinese? 坐火车 Chinese pronunciation, 坐火车 Chinese learning
- 4 How do you say "take a bus" in Chinese? 坐车 Chinese pronunciation, 坐车 Chinese learning
- 5 How to say drive in Chinese? 开车 Chinese pronunciation, 开车 Chinese learning
- 6 How do you say swimming in Chinese? 游泳 Chinese pronunciation, 游泳 Chinese learning
- 7 How do you say ride a bicycle in Chinese? 骑自行车 Chinese pronunciation, 骑自行车 Chinese learning
- 8 How do you say hello in Chinese? 你好Chinese pronunciation, 你好Chinese learning
- 9 How do you say thank you in Chinese? 谢谢Chinese pronunciation, 谢谢Chinese learning
- 10 How to say goodbye in Chinese? 再见Chinese pronunciation, 再见Chinese learning

























