SAML vs. OAuth vs. OpenID Connect
This post was initially published on my blog. Check out the original source using the link below:
Authentication and Authorisation are crucial for ensuring the security of applications and data. Three widely-used protocols for managing these processes are OAuth, SAML, and OpenID.
When you use apps like Facebook, Google, or LinkedIn to log into other websites, you’re encountering some important protocols: OAuth, SAML, and OpenID Connect. These protocols help keep your information secure while allowing you to access different services.
1. SAML (Security Assertion Markup Language)
SAML is an open standard for exchanging authentication and authorization data between parties, particularly between an identity provider (IdP) and a service provider (SP). It is primarily used for single sign-on (SSO) scenarios, enabling users to authenticate once and gain access to multiple applications.
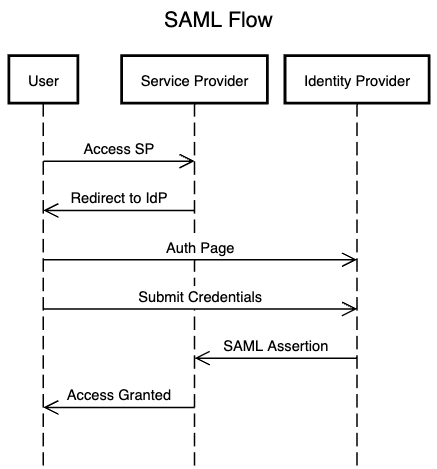
How SAML Works
Roles/Actors:
User: The individual accessing the applications.
Identity Provider (IdP): The service that authenticates the user and provides the identity assertions.
Service Provider (SP): The application or service the user is trying to access.
Request Flow Diagram:
Key Features of SAML
Single Sign-On (SSO): Users authenticate once for multiple services.
XML-Based: Uses XML for messages, making it robust.
Secure Assertions: Transmits user identity and attributes securely.
2. OAuth (Open Authorisation)
OAuth is an open standard for access delegation commonly used for token-based authentication and authorisation. It allows third-party applications to access user data without exposing their credentials. OAuth is primarily used for authorisation, enabling users to grant limited access to their resources hosted on one site to another site.
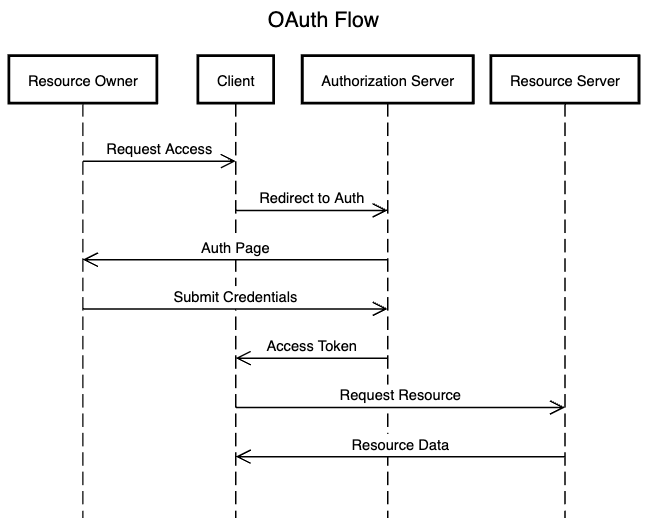
How OAuth Works
Roles/Actors:
Resource Owner: The user who owns the data and grants access to it.
Resource Server: The server hosting the user's data (e.g., Google, Facebook).
Client: The third-party application requesting access to the user's data.
Authorization Server: The server responsible for issuing access tokens to the client after authenticating the resource owner.
Request Flow Diagram:
Key Features of OAuth
Delegated Access: Users can grant access without sharing credentials.
Access Tokens: Short-lived tokens that limit access duration.
Scopes: Define the extent of access granted to the client.
3. OpenID Connect
OpenID Connect is an authentication layer built on top of OAuth 2.0. It adds identity verification and provides a way for clients to verify the identity of the user based on the authentication performed by an Authorisation Server.
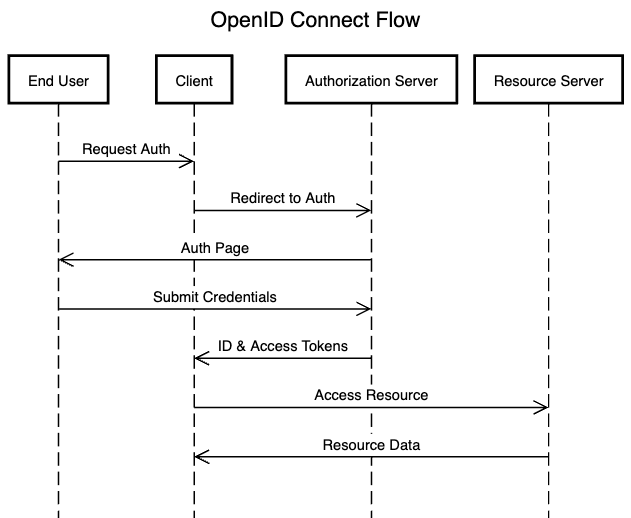
How OpenID Connect Works
Roles/Actors:
End User: The user who wants to authenticate.
Client: The application requesting user authentication.
Authorisation Server: The server that authenticates the user and issues tokens.
Request Flow Diagram:
Key Features of OpenID Connect
ID Tokens: JWTs that provide user information and claims.
Seamless Integration with OAuth: Combines authentication and authorisation.
User Info Endpoint: Allows fetching additional user information.
OpenID Connect and OAuth
Seems similar but they both serve different but complementary purposes:
OAuth: Used for authorisation. It allows apps to access resources (like your profile or photos) from another service (e.g., Facebook or Google) without needing your password. Use OAuth when you want to grant limited access to your data (e.g., a third-party app accessing your calendar).
OpenID Connect (OIDC): Built on top of OAuth, it's used for authentication. It verifies your identity and allows apps to know who you are. Use OpenID Connect when you need to log in to a website or app using a service like Google, proving who you are.
When to Use:
-
Use OAuth:
- When you want an app to access data or resources on your behalf (e.g., an app posting on Twitter for you).
- "Can this app access my data?" (Authorisation)
-
Use OpenID Connect:
- When you need to verify a user's identity (e.g., signing into a website using your Google account).
- "Who is this user?" (Authentication)
Quick Comparison of OAuth, SAML, and OpenID Connect
| Feature | OAuth | SAML | OpenID Connect |
|---|---|---|---|
| Purpose | Authorization | Authentication | Authentication & Authorization |
| Format | JSON, Token | XML | JSON |
| Use Cases | API access, Mobile apps | Web applications, SSO | Web and mobile applications |
| Complexity | Moderate | High | Moderate |
| User Experience | Redirects to IdP | Redirects to IdP | Redirects to Authorisation Server |
Conclusion
Understanding OAuth, SAML, and OpenID Connect is essential for building secure applications that handle user authentication and authorisation effectively. Each protocol has its purpose, ensuring you can access what you need while keeping your data safe.
References
OAuth 2.0 Explained Simply
What is SAML?
OpenID Connect Overview
Understanding the Differences: OAuth, SAML, and OpenID Connect
-
 How to Handle User Input in Java's Full-Screen Exclusive Mode?Handling User Input in Full Screen Exclusive Mode in JavaIntroductionWhen running a Java application in full screen exclusive mode, the usual event ha...Programming Posted on 2025-03-25
How to Handle User Input in Java's Full-Screen Exclusive Mode?Handling User Input in Full Screen Exclusive Mode in JavaIntroductionWhen running a Java application in full screen exclusive mode, the usual event ha...Programming Posted on 2025-03-25 -
 How can I safely concatenate text and values when constructing SQL queries in Go?Concatenating Text and Values in Go SQL QueriesWhen constructing a text SQL query in Go, there are certain syntax rules to follow when concatenating s...Programming Posted on 2025-03-25
How can I safely concatenate text and values when constructing SQL queries in Go?Concatenating Text and Values in Go SQL QueriesWhen constructing a text SQL query in Go, there are certain syntax rules to follow when concatenating s...Programming Posted on 2025-03-25 -
 How to Correctly Use LIKE Queries with PDO Parameters?Using LIKE Queries in PDOWhen trying to implement LIKE queries in PDO, you may encounter issues like the one described in the query below:$query = &qu...Programming Posted on 2025-03-25
How to Correctly Use LIKE Queries with PDO Parameters?Using LIKE Queries in PDOWhen trying to implement LIKE queries in PDO, you may encounter issues like the one described in the query below:$query = &qu...Programming Posted on 2025-03-25 -
 How Can I Programmatically Select All Text Within a DIV on Mouse Click?Programmatically Selecting DIV Text on Mouse ClickQuestionGiven a DIV element with text content, how can the user programmatically select the entire t...Programming Posted on 2025-03-25
How Can I Programmatically Select All Text Within a DIV on Mouse Click?Programmatically Selecting DIV Text on Mouse ClickQuestionGiven a DIV element with text content, how can the user programmatically select the entire t...Programming Posted on 2025-03-25 -
 Is There a Performance Difference Between Using a For-Each Loop and an Iterator for Collection Traversal in Java?For Each Loop vs. Iterator: Efficiency in Collection TraversalIntroductionWhen traversing a collection in Java, the choice arises between using a for-...Programming Posted on 2025-03-25
Is There a Performance Difference Between Using a For-Each Loop and an Iterator for Collection Traversal in Java?For Each Loop vs. Iterator: Efficiency in Collection TraversalIntroductionWhen traversing a collection in Java, the choice arises between using a for-...Programming Posted on 2025-03-25 -
 How to Combine Data from Three MySQL Tables into a New Table?mySQL: Creating a New Table from Data and Columns of Three TablesQuestion:How can I create a new table that combines selected data from three existing...Programming Posted on 2025-03-25
How to Combine Data from Three MySQL Tables into a New Table?mySQL: Creating a New Table from Data and Columns of Three TablesQuestion:How can I create a new table that combines selected data from three existing...Programming Posted on 2025-03-25 -
 How to Convert a Pandas DataFrame Column to DateTime Format and Filter by Date?Transform Pandas DataFrame Column to DateTime FormatScenario:Data within a Pandas DataFrame often exists in various formats, including strings. When w...Programming Posted on 2025-03-25
How to Convert a Pandas DataFrame Column to DateTime Format and Filter by Date?Transform Pandas DataFrame Column to DateTime FormatScenario:Data within a Pandas DataFrame often exists in various formats, including strings. When w...Programming Posted on 2025-03-25 -
 How to Redirect Multiple User Types (Students, Teachers, and Admins) to Their Respective Activities in a Firebase App?Red: How to Redirect Multiple User Types to Respective ActivitiesUnderstanding the ProblemIn a Firebase-based voting app with three distinct user type...Programming Posted on 2025-03-25
How to Redirect Multiple User Types (Students, Teachers, and Admins) to Their Respective Activities in a Firebase App?Red: How to Redirect Multiple User Types to Respective ActivitiesUnderstanding the ProblemIn a Firebase-based voting app with three distinct user type...Programming Posted on 2025-03-25 -
 How Can You Define Variables in Laravel Blade Templates Elegantly?Defining Variables in Laravel Blade Templates with EleganceUnderstanding how to assign variables in Blade templates is crucial for storing data for la...Programming Posted on 2025-03-25
How Can You Define Variables in Laravel Blade Templates Elegantly?Defining Variables in Laravel Blade Templates with EleganceUnderstanding how to assign variables in Blade templates is crucial for storing data for la...Programming Posted on 2025-03-25 -
 How Can I Efficiently Create Dictionaries Using Python Comprehension?Python Dictionary ComprehensionIn Python, dictionary comprehensions offer a concise way to generate new dictionaries. While they are similar to list c...Programming Posted on 2025-03-25
How Can I Efficiently Create Dictionaries Using Python Comprehension?Python Dictionary ComprehensionIn Python, dictionary comprehensions offer a concise way to generate new dictionaries. While they are similar to list c...Programming Posted on 2025-03-25 -
 Why Does PHP's DateTime::modify('+1 month') Produce Unexpected Results?Modifying Months with PHP DateTime: Uncovering the Intended BehaviorWhen working with PHP's DateTime class, adding or subtracting months may not a...Programming Posted on 2025-03-25
Why Does PHP's DateTime::modify('+1 month') Produce Unexpected Results?Modifying Months with PHP DateTime: Uncovering the Intended BehaviorWhen working with PHP's DateTime class, adding or subtracting months may not a...Programming Posted on 2025-03-25 -
 How Can I Customize Compilation Optimizations in the Go Compiler?Customizing Compilation Optimizations in Go CompilerThe default compilation process in Go follows a specific optimization strategy. However, users may...Programming Posted on 2025-03-25
How Can I Customize Compilation Optimizations in the Go Compiler?Customizing Compilation Optimizations in Go CompilerThe default compilation process in Go follows a specific optimization strategy. However, users may...Programming Posted on 2025-03-25 -
 How Can I Efficiently Read a Large File in Reverse Order Using Python?Reading a File in Reverse Order in PythonIf you're working with a large file and need to read its contents from the last line to the first, Python...Programming Posted on 2025-03-25
How Can I Efficiently Read a Large File in Reverse Order Using Python?Reading a File in Reverse Order in PythonIf you're working with a large file and need to read its contents from the last line to the first, Python...Programming Posted on 2025-03-25 -
 How Can I Synchronously Iterate and Print Values from Two Equal-Sized Arrays in PHP?Synchronously Iterating and Printing Values from Two Arrays of the Same SizeWhen creating a selectbox using two arrays of equal size, one containing c...Programming Posted on 2025-03-25
How Can I Synchronously Iterate and Print Values from Two Equal-Sized Arrays in PHP?Synchronously Iterating and Printing Values from Two Arrays of the Same SizeWhen creating a selectbox using two arrays of equal size, one containing c...Programming Posted on 2025-03-25 -
 How Do I Efficiently Select Columns in Pandas DataFrames?Selecting Columns in Pandas DataframesWhen dealing with data manipulation tasks, selecting specific columns becomes necessary. In Pandas, there are va...Programming Posted on 2025-03-25
How Do I Efficiently Select Columns in Pandas DataFrames?Selecting Columns in Pandas DataframesWhen dealing with data manipulation tasks, selecting specific columns becomes necessary. In Pandas, there are va...Programming Posted on 2025-03-25
Study Chinese
- 1 How do you say "walk" in Chinese? 走路 Chinese pronunciation, 走路 Chinese learning
- 2 How do you say "take a plane" in Chinese? 坐飞机 Chinese pronunciation, 坐飞机 Chinese learning
- 3 How do you say "take a train" in Chinese? 坐火车 Chinese pronunciation, 坐火车 Chinese learning
- 4 How do you say "take a bus" in Chinese? 坐车 Chinese pronunciation, 坐车 Chinese learning
- 5 How to say drive in Chinese? 开车 Chinese pronunciation, 开车 Chinese learning
- 6 How do you say swimming in Chinese? 游泳 Chinese pronunciation, 游泳 Chinese learning
- 7 How do you say ride a bicycle in Chinese? 骑自行车 Chinese pronunciation, 骑自行车 Chinese learning
- 8 How do you say hello in Chinese? 你好Chinese pronunciation, 你好Chinese learning
- 9 How do you say thank you in Chinese? 谢谢Chinese pronunciation, 谢谢Chinese learning
- 10 How to say goodbye in Chinese? 再见Chinese pronunciation, 再见Chinese learning

 rahulvijayvergiya.hashnode.dev
rahulvijayvergiya.hashnode.dev
























