Stateful vs. Stateless Authentication
Stateless and Stateful Architecture
Refers to the state of the application, that is, the condition or quality of it at a given time. In stateless authentication, there is no session or user stored, containing only static contents. This differs from stateful, which is dynamic content.
A stateless process is an isolated resource, which does not reference any other service or interaction with another system. It operates only in that part of the code, without bringing information from old transactions, as stateless authentication does not store this type of data; each operation is done from scratch.
Stateful authentication allows information to be used more than once and is executed based on the context of previous transactions. Therefore, in applications where it is necessary to wait for a response or preexisting data, whether present in another system or database, stateful is used.
Stateless Authentication
Stateless authentication consists of a strategy in which, after providing credentials, the user receives an access token in response. This token already contains all the information necessary to identify the user who generated it, without the need to continually consult the service that issued the token or a database.
This token is stored client-side (browser), so the server only has the ability to check the validity of the token by confirming that the payload and signature match.
Stateless Authentication JWT
JSON Web Token (JWT) are keys with standards established in RFC-7519, containing an entity in the form of declarations, which are independent, without the need to call the server to revalidate the token.
Are strings encoded in the base64 standard using a secret key, as in the example:
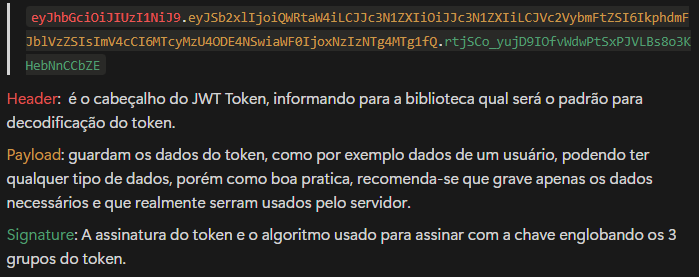
Advantages and Disadvantages
Advantages:
- Low server memory consumption.
- Excellent in terms of scalability.
- Ideal for distributed applications, such as APIs and microservices.
- Generation and distribution of the token in an isolated application, without dependence on third parties.
- Easy interpretation and validation of token user data.
Disadvantages:
- Difficulty in access control.
- It is not possible to revoke the token at any time easily.
- It can facilitate the entry of malicious third parties, if someone has access to the token.
- The session cannot be changed until the token expires.
- The JWT token is more complex and may become unnecessary in centralized applications, such as monoliths.
Stateful authentication
Commonly used in various applications, especially those that do not require as much scalability, the stateful session is created in the back-end of the application, and the session reference is sent back to the corresponding user. Each time the user makes a request, part of the application generates the token. From that moment on, with each new request, this token will be sent again to the application to revalidate access. In this model, if there is any change in user data, the token can be easily revoked.
These are opaque access tokens, that is, a simple string in a proprietary format that does not contain any identifier or user data relating to that token. The recipient needs to call the server that created the token to validate it.
Example token: 8c90e55a-e867-45d5-9e42-8fcbd9c30a74
This ID must be stored in a database with the user who owns the token.
Advantages and Disadvantages
Advantages:
- Centralized implementation logic.
- Simplified access management and control.
- Excellent for monoliths, MVC applications and internal processes.
- More secure against malicious third parties.
Disadvantages:
- There may be an overload in the API responsible for validating the token.
- Failure in terms of scalability.
- Greater difficulty in distributing authentication between microservices.
- In a distributed application, if the authentication service fails, all other services become unavailable.
- Greater implementation complexity.
- Greater difficulty in integrating with third-party systems.
When to use each approach?
When to use a JWT Token and Stateless Authentication
- When greater performance is needed without worrying about overloading an API.
- When there are several communications distributed between services.
- When it is necessary to identify which user is performing an action in the system in different services.
- When it is not intended to persist a user's data, only their initial registration.
- If it is necessary to generate external access to the service.
- If it is necessary to manipulate the data of whoever is performing a certain action with minimal impact on the system.
When to use an Opaque Token and Stateful Authentication
- If full access control of users of a system is necessary, mainly to define access hierarchy.
- In a centralized application, without distributed services and without communication with external services.
Final Considerations:
- In some places, such as "API stress", the term may be replaced with "API overhead" for clarity.
- The section on "JWT Token" could include a more detailed explanation of what the "declarations" mentioned in RFC-7519 are, if the target audience needs more context.
- In the section on stateful authentication, the phrase "one part of the application will generate the token" could be clarified by explaining which specific part of the application is responsible for this.
-
 Why is My Tomcat Server Showing \"Several Ports Required are Already in Use\"?Tomcat Server Port Conflict: Resolving Error "Several Ports Required are Already in Use"When attempting to launch a JSP program on Tomcat in...Programming Published on 2024-11-17
Why is My Tomcat Server Showing \"Several Ports Required are Already in Use\"?Tomcat Server Port Conflict: Resolving Error "Several Ports Required are Already in Use"When attempting to launch a JSP program on Tomcat in...Programming Published on 2024-11-17 -
 How to Determine File Creation Date in Java?Determining File Creation Date in Java: Uncovering File MetadataDetermining the creation date of a file can be a valuable piece of information, especi...Programming Published on 2024-11-17
How to Determine File Creation Date in Java?Determining File Creation Date in Java: Uncovering File MetadataDetermining the creation date of a file can be a valuable piece of information, especi...Programming Published on 2024-11-17 -
 How to Synchronize Timezones in PHP and MySQL?Synchronizing Timezones in PHP and MySQLYou are developing an application that requires storing dates in MySQL using the PHP date() function. Comparin...Programming Published on 2024-11-17
How to Synchronize Timezones in PHP and MySQL?Synchronizing Timezones in PHP and MySQLYou are developing an application that requires storing dates in MySQL using the PHP date() function. Comparin...Programming Published on 2024-11-17 -
 How Can We Implement Jagged Arrays in C/C++?Understanding Jagged Arrays in C/C While the concept of jagged arrays, where rows can have varying lengths, is not directly supported in standard C/C...Programming Published on 2024-11-17
How Can We Implement Jagged Arrays in C/C++?Understanding Jagged Arrays in C/C While the concept of jagged arrays, where rows can have varying lengths, is not directly supported in standard C/C...Programming Published on 2024-11-17 -
 How Can I Get User Input in Sublime Text 2?User Input in Sublime Text 2Users encounter difficulties when attempting to input values in Sublime Text 2, particularly when using functions like inp...Programming Published on 2024-11-17
How Can I Get User Input in Sublime Text 2?User Input in Sublime Text 2Users encounter difficulties when attempting to input values in Sublime Text 2, particularly when using functions like inp...Programming Published on 2024-11-17 -
 How to Fix \"ImproperlyConfigured: Error loading MySQLdb module\" in Django on macOS?MySQL Improperly Configured: The Problem with Relative PathsWhen running python manage.py runserver in Django, you may encounter the following error:I...Programming Published on 2024-11-17
How to Fix \"ImproperlyConfigured: Error loading MySQLdb module\" in Django on macOS?MySQL Improperly Configured: The Problem with Relative PathsWhen running python manage.py runserver in Django, you may encounter the following error:I...Programming Published on 2024-11-17 -
 Beyond `if` Statements: Where Else Can a Type with an Explicit `bool` Conversion Be Used Without Casting?Contextual Conversion to bool Allowed Without a CastYour class defines an explicit conversion to bool, enabling you to use its instance 't' di...Programming Published on 2024-11-17
Beyond `if` Statements: Where Else Can a Type with an Explicit `bool` Conversion Be Used Without Casting?Contextual Conversion to bool Allowed Without a CastYour class defines an explicit conversion to bool, enabling you to use its instance 't' di...Programming Published on 2024-11-17 -
 How Can I Execute PHP Code Stored in a MySQL Database?Executing PHP Stored in MySQL DatabaseExecuting PHP stored in a MySQL database presents a unique challenge in web development. To perform this operati...Programming Published on 2024-11-17
How Can I Execute PHP Code Stored in a MySQL Database?Executing PHP Stored in MySQL DatabaseExecuting PHP stored in a MySQL database presents a unique challenge in web development. To perform this operati...Programming Published on 2024-11-17 -
 What Happened to Column Offsetting in Bootstrap 4 Beta?Bootstrap 4 Beta: The Removal and Restoration of Column OffsettingBootstrap 4, in its Beta 1 release, introduced significant changes to the way column...Programming Published on 2024-11-17
What Happened to Column Offsetting in Bootstrap 4 Beta?Bootstrap 4 Beta: The Removal and Restoration of Column OffsettingBootstrap 4, in its Beta 1 release, introduced significant changes to the way column...Programming Published on 2024-11-17 -
 How Can I Find Users with Today\'s Birthdays Using MySQL?How to Identify Users with Today's Birthdays Using MySQLDetermining if today is a user's birthday using MySQL involves finding all rows where ...Programming Published on 2024-11-17
How Can I Find Users with Today\'s Birthdays Using MySQL?How to Identify Users with Today's Birthdays Using MySQLDetermining if today is a user's birthday using MySQL involves finding all rows where ...Programming Published on 2024-11-17 -
 How to Handle Return Type Conflicts in PHP 8.1?Reference: Return Type Conflict vs. #[\ReturnTypeWillChange] AttributeContext:In PHP 8.1, specifying return types for methods becomes more prevalent, ...Programming Published on 2024-11-17
How to Handle Return Type Conflicts in PHP 8.1?Reference: Return Type Conflict vs. #[\ReturnTypeWillChange] AttributeContext:In PHP 8.1, specifying return types for methods becomes more prevalent, ...Programming Published on 2024-11-17 -
 Using WebSockets in Go for Real-Time CommunicationBuilding apps that require real-time updates—like chat applications, live notifications, or collaborative tools—requires a communication method faster...Programming Published on 2024-11-17
Using WebSockets in Go for Real-Time CommunicationBuilding apps that require real-time updates—like chat applications, live notifications, or collaborative tools—requires a communication method faster...Programming Published on 2024-11-17 -
 How to Correctly Transfer Files Over Sockets in Java?Java File Transfer over Sockets: Sending and Receiving Byte ArraysIn Java, transferring files over sockets involves converting the file into byte arra...Programming Published on 2024-11-17
How to Correctly Transfer Files Over Sockets in Java?Java File Transfer over Sockets: Sending and Receiving Byte ArraysIn Java, transferring files over sockets involves converting the file into byte arra...Programming Published on 2024-11-17 -
 Why Use `enableReaderMode` API for Writing NDEF Records to NFC Tags?How to Write NDEF Records to NFC TagWriting NDEF records to an NFC tag requires utilizing the enableReaderMode API, which offers superior performance ...Programming Published on 2024-11-17
Why Use `enableReaderMode` API for Writing NDEF Records to NFC Tags?How to Write NDEF Records to NFC TagWriting NDEF records to an NFC tag requires utilizing the enableReaderMode API, which offers superior performance ...Programming Published on 2024-11-17 -
 Here are some question-style titles that fit the content of your article: * MySQLdb on Mac OS X: Why am I getting \"Library not loaded: libmysqlclient.16.dylib\"? * How to Fix \"Library not loaded: lPython: MySQLdb and "Library not loaded: libmysqlclient.16.dylib"In an attempt to develop Python/Django applications, you've encountered...Programming Published on 2024-11-17
Here are some question-style titles that fit the content of your article: * MySQLdb on Mac OS X: Why am I getting \"Library not loaded: libmysqlclient.16.dylib\"? * How to Fix \"Library not loaded: lPython: MySQLdb and "Library not loaded: libmysqlclient.16.dylib"In an attempt to develop Python/Django applications, you've encountered...Programming Published on 2024-11-17
Study Chinese
- 1 How do you say "walk" in Chinese? 走路 Chinese pronunciation, 走路 Chinese learning
- 2 How do you say "take a plane" in Chinese? 坐飞机 Chinese pronunciation, 坐飞机 Chinese learning
- 3 How do you say "take a train" in Chinese? 坐火车 Chinese pronunciation, 坐火车 Chinese learning
- 4 How do you say "take a bus" in Chinese? 坐车 Chinese pronunciation, 坐车 Chinese learning
- 5 How to say drive in Chinese? 开车 Chinese pronunciation, 开车 Chinese learning
- 6 How do you say swimming in Chinese? 游泳 Chinese pronunciation, 游泳 Chinese learning
- 7 How do you say ride a bicycle in Chinese? 骑自行车 Chinese pronunciation, 骑自行车 Chinese learning
- 8 How do you say hello in Chinese? 你好Chinese pronunciation, 你好Chinese learning
- 9 How do you say thank you in Chinese? 谢谢Chinese pronunciation, 谢谢Chinese learning
- 10 How to say goodbye in Chinese? 再见Chinese pronunciation, 再见Chinese learning

























